Essential tools for image forensics

Learn how the tools used to analyze images work.
Today, digital images play a fundamental role in society, acquiring increasing relevance in judicial processes. Therefore, it is essential to verify the authenticity of a digital photograph, since it can be considered evidence in legal proceedings.
In this article, we will explore some image forensics tools, as well as provide brief examples of how to use each of them.
Exiftool: Permalink
Exiftool is a powerful tool that allows us to analyze the metadata of files and images. In the case of images, this tool can provide us with valuable information, such as the type of file, the date the photo was taken and the location where the image was captured, etc. Sometimes you might find data encoded in base64 format.
Installation:
sudo apt install libimage-exiftool-perl
Ejemplo de uso:
exiftool <image or file name>
┌─[r00tbr4ck3r@parrot]─[~/Forensic]
└──╼ $exiftool cat.png
ExifTool Version Number : 12.16
File Name : cat.png
Directory : .
File Size : 858 KiB
File Modification Date/Time : 2023:10:23 20:59:54-05:00
File Access Date/Time : 2023:10:23 20:59:54-05:00
File Inode Change Date/Time : 2023:10:23 20:59:54-05:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.02
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Current IPTC Digest : 7a78f3d9cfb1ce42ab5a3aa30573d617
Copyright Notice : PicoCTF
Application Record Version : 4
XMP Toolkit : Image::ExifTool 10.80
License : cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9
Rights : PicoCTF
Image Width : 2560
Image Height : 1598
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 2560x1598
Megapixels : 4.1
Forensically: Permalink
Forensically is an online tool with a set of features that make it an essential tool for image forensics. Like Burp Suite in the world of web security, Forensically is a platform that allows you to upload images and access a wide range of tools. These include a magnifying glass for inspecting minute details, clone detection, noise analysis, metadata visualization, string extraction, and many others. This tool can help you see if it was a manipulated image among much more.
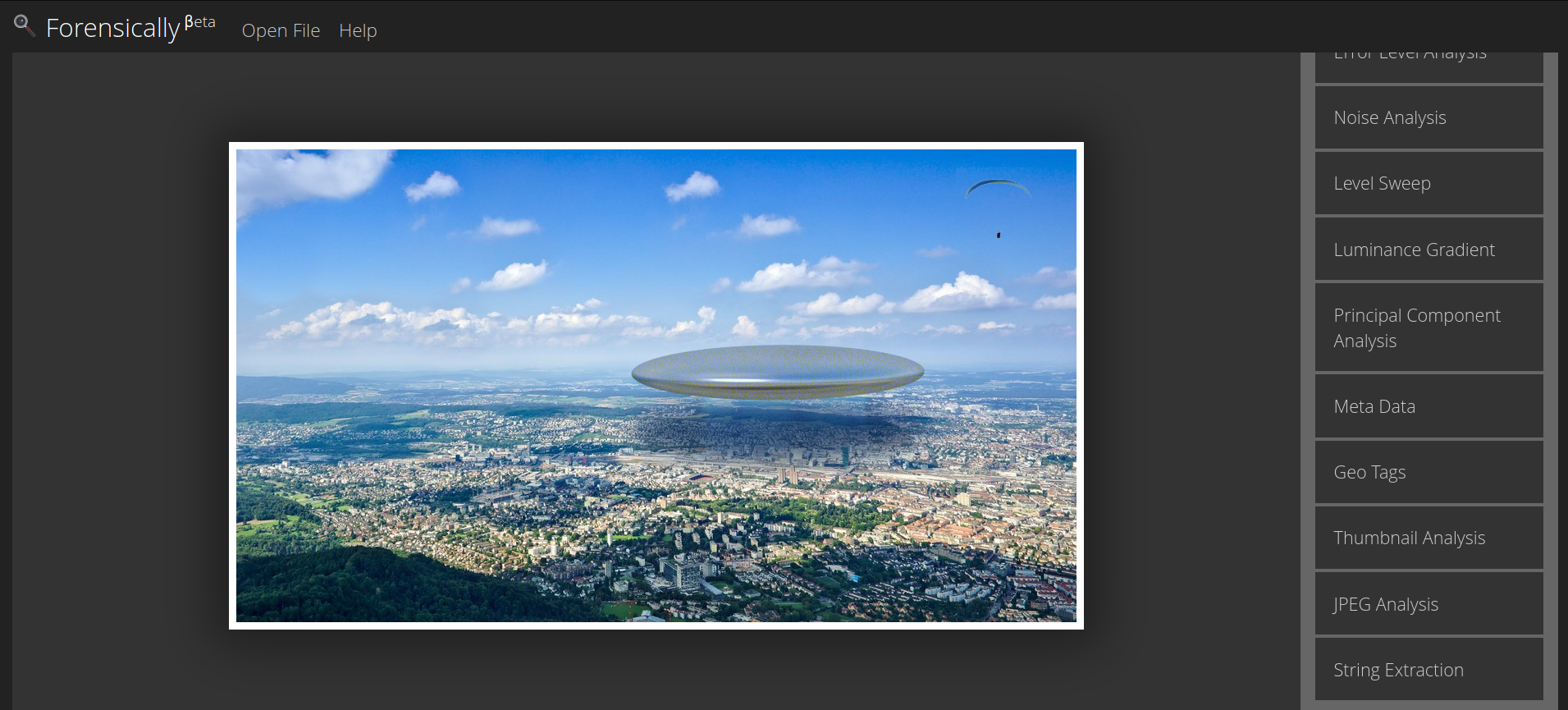
Forensically
Xxd: Permalink
This tool allows you to examine the hexadecimal characters and strings contained in the image. Additionally, it provides the ability to parse hexadecimal data using what is known as “Magic Bytes.” Simply put, these “Magic Bytes” are sets of bytes that provide clear identification of the type of file you are analyzing. If you want more information about types of “Magic Bytes”, you can consult a reference list at the following link:
Installation:
sudo apt-get install -y xxd
Usage example:
xxd <file name> | less
In this result, we can see that the file is actually not a .png file, but a JPEG file. This conclusion is based on review of the magic bytes that indicate the file format. To verify this, we can consult the list of magic bytes:
─[r00tbr4ck3r@parrot]─[~/Forensic]
└──╼ $xxd cat.png | less
00000000: ffd8 ffe0 0010 4a46 4946 0001 0200 0001 ......JFIF......
00000010: 0001 0000 ffed 0030 5068 6f74 6f73 686f .......0Photosho

Magic
Binwalk: Permalink
Its main function is to identify files and codes hidden within firmware images. Binwalk uses advanced search techniques to scan firmware images for embedded data, executable code, and more:
Installation:
sudo apt install binwalk
Usage example:
binwalk <nombre de la imagen>
┌─[r00tbr4ck3r@parrot]─[~/Forensic]
└──╼ $binwalk dolls.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 594 x 1104, 8-bit/color RGBA, non-interlaced
3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8
272492 0x4286C Zip archive data, at least v2.0 to extract, compressed size: 378954, uncompressed size: 383940, name: base_images/2_c.jpg
651612 0x9F15C End of Zip archive, footer length: 22
┌─[r00tbr4ck3r@parrot]─[~/Forensic]
└──╼ $
In this example, we explore a picoCTF challenge involving an image containing multiple embedded ZIP files. To tackle this task, we will employ the binwalk command with two key parameters: -e to extract and -M to enable recursive extraction. This process will allow us to decompress the ZIP files contained in the image called “dolls.jpg”.
┌─[✗]─[r00tbr4ck3r@parrot]─[~/Forensic]
└──╼ $binwalk -e -M dolls.jpg
Scan Time: 2023-10-23 21:29:37
Target File: /home/r00tbr4ck3r/Forensic/dolls.jpg
MD5 Checksum: 4e20dca670f35285995d96533d0e0a69
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 594 x 1104, 8-bit/color RGBA, non-interlaced
3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8
272492 0x4286C Zip archive data, at least v2.0 to extract, compressed size: 378954, uncompressed size: 383940, name: base_images/2_c.jpg
651612 0x9F15C End of Zip archive, footer length: 22
Scan Time: 2023-10-23 21:29:37
Target File: /home/r00tbr4ck3r/Forensic/_dolls.jpg.extracted/base_images/2_c.jpg
MD5 Checksum: 4d6e68a72702eba3f2b1f95670f12ac7
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 526 x 1106, 8-bit/color RGBA, non-interlaced
3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8
187707 0x2DD3B Zip archive data, at least v2.0 to extract, compressed size: 196045, uncompressed size: 201447, name: base_images/3_c.jpg
383807 0x5DB3F End of Zip archive, footer length: 22
383918 0x5DBAE End of Zip archive, footer length: 22
Scan Time: 2023-10-23 21:29:37
Target File: /home/r00tbr4ck3r/Forensic/_dolls.jpg.extracted/base_images/_2_c.jpg.extracted/base_images/3_c.jpg
MD5 Checksum: 03116a4e0101b30bedcf0905531c0e1f
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 428 x 1104, 8-bit/color RGBA, non-interlaced
3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8
123606 0x1E2D6 Zip archive data, at least v2.0 to extract, compressed size: 77653, uncompressed size: 79808, name: base_images/4_c.jpg
201425 0x312D1 End of Zip archive, footer length: 22
Scan Time: 2023-10-23 21:29:37
Target File: /home/r00tbr4ck3r/Forensic/_dolls.jpg.extracted/base_images/_2_c.jpg.extracted/base_images/_3_c.jpg.extracted/base_images/4_c.jpg
MD5 Checksum: 4e139c3a53b17b18c5fe1994dd3e7d46
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 320 x 768, 8-bit/color RGBA, non-interlaced
3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8
79578 0x136DA Zip archive data, at least v2.0 to extract, compressed size: 64, uncompressed size: 81, name: flag.txt
79786 0x137AA End of Zip archive, footer length: 22
And here the result is presented, which in this case corresponds to the “flag”, an essential element in challenges of this type. The flag found is shown below:
┌─[r00tbr4ck3r@parrot]─[~/Forensic/_dolls.jpg.extracted/base_images/_2_c.jpg.extracted/base_images/_3_c.jpg.extracted/base_images/_4_c.jpg.extracted]
└──╼ $cat flag.txt
picoCTF{xxxxxxxxxxxxx}
Conclusion: Permalink
In this article we have explored a variety of tools that are essential for image forensics. These tools play a crucial role in verifying the authenticity of digital photographs, which is essential in a wide range of contexts, from cybersecurity to solving challenges such as CTFs.
If you would like a more detailed analysis of any of these tools in the future, please feel free to contact me via direct message (DM). I am available to provide additional information and guidance in using these tools.
